Our Managed Security & Reporting Services
QCM offers monthly Managed Security and Reporting Services to help small and medium-sized businesses with their IT Security and Compliance. Many SMB businesses do not have the available staff or the ability to continually manage and secure their IT infrastructure that protects their company and their customer’s valuable data. Few have policies in place to respond to a data breach. Left unprotected or ill-protected, a small business can be held liable for stored customer data affected by a breach.
Most standard cybersecurity companies offer standard protection such as Firewall, Anti-virus, Patching, and Spam Filtering that cover standard external threats, but in actuality, most security issues stem from internal threats.
Did You Know?
In all, internal vulnerabilities in some form or another are responsible for a total of 70% of all data breaches
(source: https://blog.trendmicro.com/most-data-security-threats-are-internal-forrester-says/)
In ransomware attacks, the most common points of entry were phishing (53%), unpatched servers/VPN (38%), and credential theft (29%)
(source: https://www.insurancebusinessmag.com/us/news/cyber/despite-awareness-small-businesses-still-highly-vulnerable-to-cyber-attacks-474678.aspx)
Looking for other Security and Compliance Options? Cyber skills development or Managed Services? We offer additional services to help you.
EMAIL US info@qcmtech.com
USE OUR CONTACT FORM
CALL US - If your situation is urgent, please reach out to Tim Kinnerup for assistance
Tim Kinnerup, Sr. Vice President
(480) 483-4371 Direct
Why Security Matters to Businesses Like Yours
Can You Afford these Numbers?
- 41% of small businesses fell victim to a cyber attack in 2023, a rise from 38% in the 2022 report and close to double from 22% in 2021
- US small businesses paid over $16,000 in cyber ransoms over the past 12 months. For businesses who paid ransoms, only half (50%) recovered all their data and half (50%) were forced to rebuild systems
- Over a quarter of businesses (27%) who paid ransoms were attacked again and 27% went on to be asked for more money by the attacker
Source: https://www.hiscox.com/cybersecurity
How will Your Customers React?
- 33% of firms required 3+ days to recover from attack ¹
- 60% of SMBs fail within 6 months of being hacked ¹
- Customers and suppliers quickly lose confidence in a business following a ransomware attack, especially when hackers obtain their confidential data stored by the business. After an attack, customers are often suspicious that the business was somehow negligent because they did not have secure data protection systems in place. A direct consequence of this loss of confidence is that the SMB’s customers start to feel vulnerable and take their business elsewhere ²
Source #1: https://www.sec.gov/news/statement/cybersecurity-challenges-for-small-midsize-businesses.html
Source #2: https://www.veeam.com/blog/small-business-ransomware.html
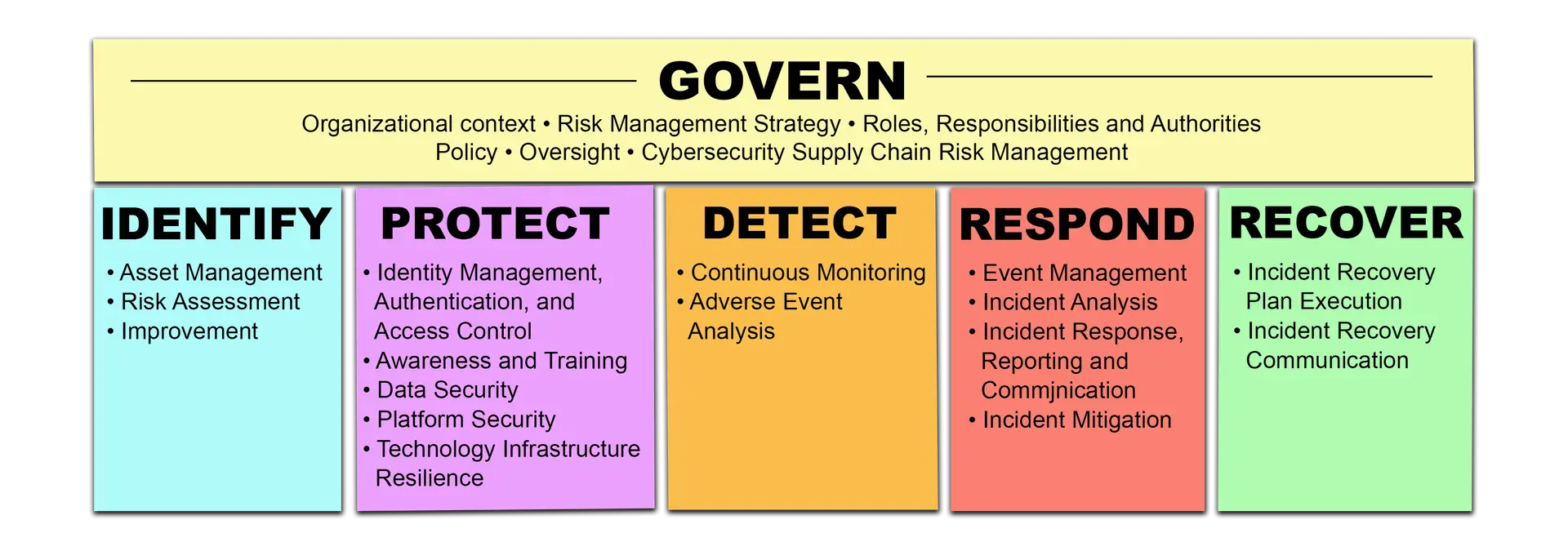
Recommended Best Practices by the NIST Cybersecurity [CSF] Framework
The Cybersecurity Framework
The core functions in the Cybersecurity Framework (CSF) — GOVERN, IDENTIFY, PROTECT, DETECT, RESPOND, and RECOVER — were selected by NIST because they represent the primary pillars for a successful and holistic cybersecurity program. They aid organizations in easily expressing their management of cybersecurity risk at a high level and enabling risk management decisions.
(Source: https://csrc.nist.gov/Projects/cybersecurity-framework/Filters#/csf/filters)
How Our Managed Security & Reporting Services Work
First, you’ll get to decide from our 3 levels of Security Reporting Services (Silver, Gold Platinum), which will determine your initial assessment and monthly services thereafter. Next, we’ll perform an assessment of your current security system at the level you decide upon. Our evaluation includes an external vulnerability scan, which addresses the major weaknesses faced by small businesses. After your assessment, we’ll show you the relative risks of what we discovered, and exactly what needs to be addressed. Next, we’ll use the NIST CSF measures to build and provide you with a recommended management plan that includes ongoing services to protect your business.
What You’ll Get with Your Managed Security & Reporting Services Plan
We enforce your IT Security Policies with regard to access control, computers, and network security. We also provide Security Alerting and continual scanning that looks for breaches behind your firewall:
- Automatically generated on a daily schedule
- Alerts sent to designated parties
- Alerts include built-in dynamic ‘action buttons’ for each threat, where you can instruct us to Remediate, Investigate, or Ignore
It Starts with Our Silver Plan, with 3 Plans to Serve Your Needs and Budget
We offer Silver, Gold, and Platinum Plans, with each covering additional internal security services. We are happy to provide you with more information on each respective plan.
We'll evaluate the following:
- Inbound Firewall configuration and search for known external vulnerabilities
- Outbound Firewall configuration
- The effectiveness of the current patch management
- Anti-virus and anti-spyware deployment
As well as:
- Administrator review
- Share permission review
- Physical security walkthrough
Value to Your Business
- More secure environment and peace of mind
- Reduced security management on your end
- Increased infrastructure reliability
- Avoid compliance fines and penalties
- Meets automation requirements for compliance frameworks
- Increase awareness of security-related issues
Now that you know how much our services can offer you at such fair pricing, reach out to us today and we’ll be happy to provide you with more information.
3 Ways to Reach Us
CALL US - If your situation is urgent, please reach out to Tim Kinnerup for assistance
Tim Kinnerup, Sr. Vice President
(480) 483-4371 Direct
EMAIL US info@qcmtech.com
CONTACT US ONLINE
Additional Resources
Framework for Improving Critical Infrastructure Cybersecurity and related news, information:
www.nist.gov/cyberframework
Additional cybersecurity resources:
http://csrc.nist.gov/
Most malware aimed at smaller businesses is focused on data theft, with password stealers, keyboard loggers, and other spyware accounting for nearly half of detected malware. The Sophos 2024 Threat Report covers these and other malware distribution mechanisms now in use, which range from phishing to malvertising and SEO poisoning. It also identifies the most common vulnerabilities attackers exploit and how the threat landscape is changing.
The report is based on the research and real-world experiences of Sophos’ threat, incident response and AI experts, and covers:
- The top cybersecurity challenges
- Latest social engineering tricks
- Dual-use tools
QCM Technologies
www.qcmtech.com
Scottsdale, Arizona • Est. 2001